Chapter #18: How to Manage Containers Using Podman and Skopeo in RHEL
In this chapter, we explore managing OCI containers on RHEL using Podman and Skopeo, including systemd integration, storage, and rootless setup.

One of the challenges developers faced in the past is getting applications to run reliably across multiple computing environments. Oftentimes, applications didn’t run as expected or encountered errors and failed altogether. And that’s where the concept of containers was born.
What are Container Images?
Container images are static files that ship with executable code that runs in an isolated environment.
A container image comprises system libraries, dependencies & other platform settings needed by the application to run in diverse environments.
Red Hat Linux provides a set of useful container tools that you can leverage to work directly with Linux containers using requiring docker commands.
These include:
- Podman - This is a daemon‑less container engine for running and managing OCI containers in either root or rootless mode. Podman is similar to Docker and has the same command options except that Docker is a daemon. You can pull, run, and manage container images using podman in much the same way as you would with Docker. Podman comes with lots of advanced features, fully integrates with systems, and offers user Namespace support which includes running containers without the need for a root user.
- Skopeo - This is a command‑line tool used for copying container images from one registry to another. You can use Skopeo to copy images to and from a particular host as well as copy images to another container registry or environment. Apart from copying images, you can use it to inspect images from various registries and use signatures to create and verify images.
- Buildah - This is a set of command‑line tools used for creating and managing container OCI images using Docker files.
In this chapter, we will focus on Managing containers using podman and Skopeo.
Running Containers as a Regular (Rootless) User (New)
Beginning with RHEL 8, Podman supports rootless containers out of the box. Running containers without elevated privileges greatly reduces security risks.
# login as an ordinary user
$ podman info --debug | grep rootless
# you should see build information confirming “rootless= true”
If it returns false, make sure that the uidmap package is installed and that the following lines exist (or are generated automatically) in /etc/subuid and /etc/subgid:
<your‑user>:100000:65536
A quick re‑login is usually enough to activate the namespace mappings. From this point forward, all the container commands shown in the rest of the chapter work the same way, only without sudo.
Searching Container Images from a Remote Registry
The podman search command allows you to search selected remote registries for container images. The default list of registries is defined in the registries.conf file located in the /etc/containers/ directory.
The registries are defined by 3 sections.
[registries.search] - This section specifies the default registries that podman can search for container images. It searches for the requested image in the registry.access.redhat.com, registry.redhat.io, and docker.io registries.
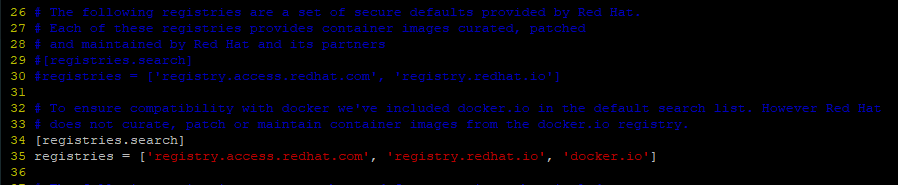
[registries.insecure] - This section specifies registries that do not implement TLS encryption, i.e. insecure registries. By default, no entries are specified.
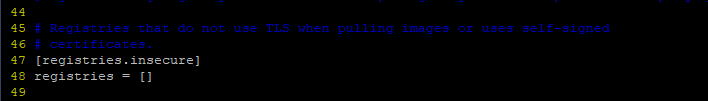
[registries.block] - This blocks or denies access to the specified registries from your local system. By default, no entries are specified.
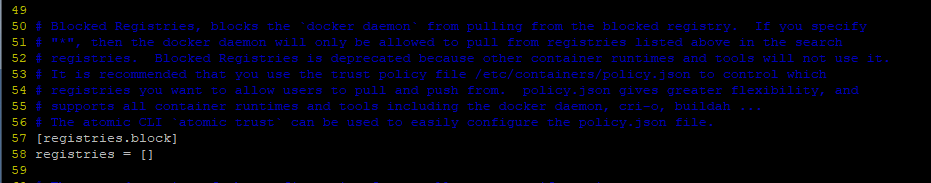
As a regular (non‑root) user running the podman command, you can define your own registries.conf file on your home directory ($HOME/.config/containers/registries.conf) to override system‑wide settings.
Rules When Specifying Registries
- Every registry should be enclosed by single quotes.
- Registries can be specified using either a hostname or IP address.
- If multiple registries are specified, then they should be separated by commas.
- If a registry uses a non‑standard port – either port TCP ports 443 for secure and 80 for insecure, – the port number should be specified alongside the registry name e.g.
registry.example.com:5566.
To search a registry for a container image using the syntax:
podman search registry/container_image
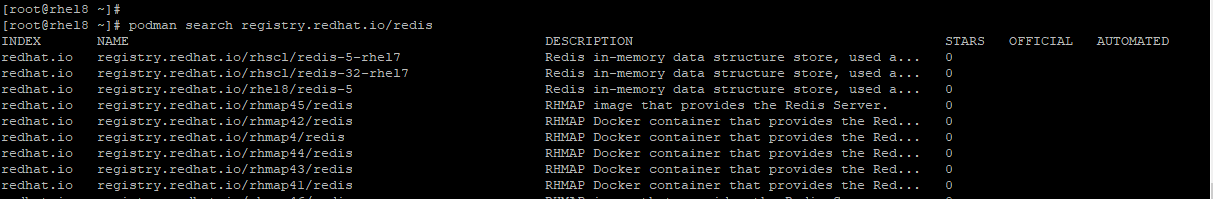
For example, to search for a Redis image in the registry.redhat.io registry, invoke the command:
podman search registry.redhat.io/redis
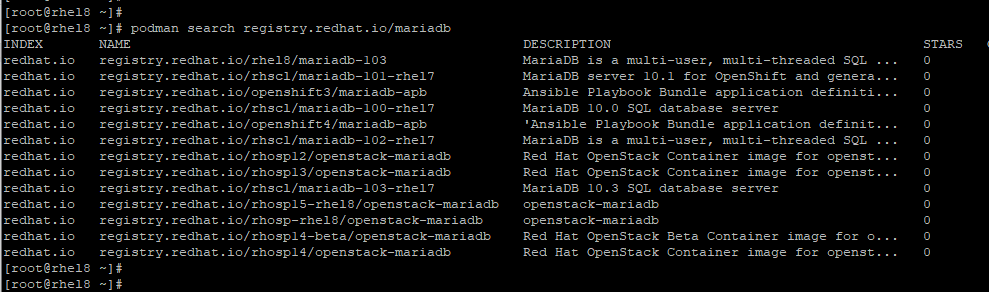
To search for a MariaDB container image run.
podman search registry.redhat.io/mariadb
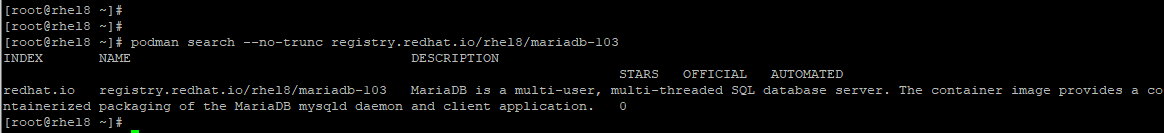
To obtain an elaborate description of a container image, use the --no-trunc option before the name of the container image from the results that you get.
For instance, we will try to obtain a detailed description of the MariaDB container image as shown:
podman search --no-trunc registry.redhat.io/rhel8/mariadb-103