Chapter #21: How to Use Ansible Modules for System Administration Tasks
In this chapter, you will learn how to simplify Linux administration using Ansible modules for package management, firewall configuration, file handling, and task automation.
In this chapter, we will go deeper and discover additional modules that are helpful in performing a number of system administration tasks.
You will get a basic idea of each module and look at the options available for accomplishing certain tasks.
Managing Software Packages and Repositories in Ansible
When installing packages on Linux systems, different distributions come with different package managers. For RedHat distributions, we have yum & dnf while for Debian flavors, there’s apt.
Ansible comes with a module called package, which eliminates the need for using different package managers for different systems. It automatically uses the corresponding package manager of the host system, thereby making work easier.
Install Software Packages
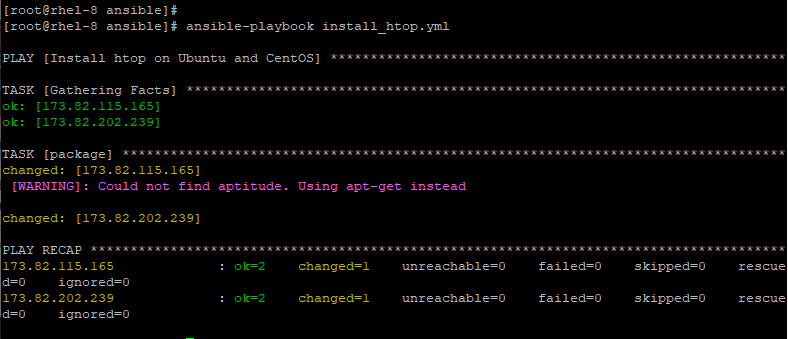
For example, to install htop in a group of hosts comprising both Debian & RedHat distros use the package module as shown in the install_htop.yml playbook below.
---
- name: Install htop on Ubuntu and CentOS
hosts: all
tasks:
- package:
name: htop
state: installed
Managing Services Using Ansible
Next, we have a service module, which is used for managing services on Linux systems. It’s used to start, stop or restart a service. You can also use it to enable a service so that when a system boots, it automatically starts the service.
Start and Enable a Service
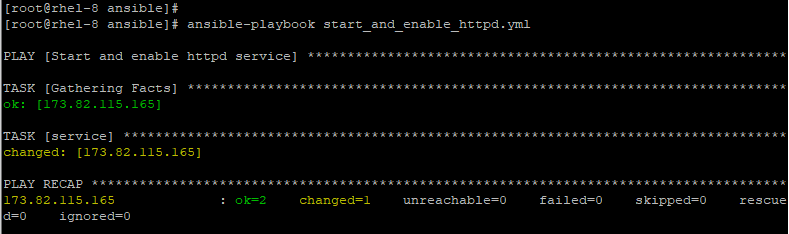
For example, to start & enable Apache webserver on RHEL, use the service as shown.
---
- name: Start and enable httpd service
hosts: webservers
tasks:
- service:
name: httpd
state: started
enabled: yes
Stop a Service
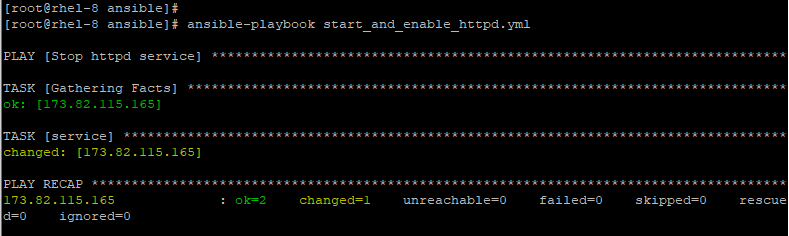
To stop httpd service, pass the stopped attribute.
---
- name: Stop httpd service
hosts: webservers
tasks:
- service:
name: httpd
state: stopped
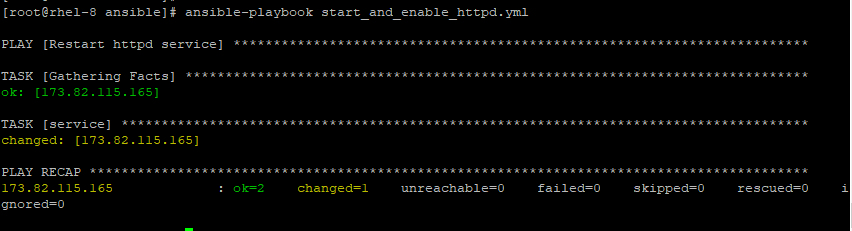
Restart a Service
To restart httpd service, pass the restarted attribute.
---
- name: Restart httpd service
hosts: webservers
tasks:
- service:
name: httpd
state: restarted
Managing Firewall with Ansible
Another important task system administrators undertake is the management of the firewall. In Ansible playbooks, this has been made much easier with firewalld and ufw modules. You can configure the firewall to allow or block a port or service or even a source address.
Let’s jump in and have a look at a few examples:
Open/Block Port 80 in firewalld
In the playbook below, port 80 is allowed across the firewall.
The option permanent: yes enforces the firewall rule and makes it persistent across reboots. However, this rule does not apply immediately. It only comes into effect after a reboot. To enforce the rule immediately, use the option immediate: yes.
---
- name: Allow port 80
hosts: webservers
tasks:
- firewalld:
port: 80/tcp
permanent: yes
state: enabled
To specify the addresses allowed, use the source: 0.0.0.0/0 statement.
- firewalld:
source: 192.168.0.0/24
zone: public
state: enabled
To specify a range of ports to be allowed use the port option as follows:
- firewalld:
port: 213-567/udp
permanent: yes
state: enabled
To block the port change the state option to disabled as shown:
- firewalld:
port: 80/tcp
permanent: yes
state: disabled