Chapter #16: How SELinux and AppArmor Improve Linux Security
In this article, you’ll learn SELinux vs AppArmor differences, how to configure modes, manage profiles, and troubleshoot permissions on CentOS, Ubuntu, and openSUSE.
To overcome the limitations of and to increase the security mechanisms provided by standard ugo/rwx permissions and access control lists, the United States National Security Agency (NSA) devised a flexible Mandatory Access Control (MAC) method known as SELinux (short for Security Enhanced Linux).
To restrict, among other things, the ability of processes to access or perform other operations on system objects (such as files, directories, network ports, etc) to the least permission possible, while still allowing for later modifications to this model.
Another popular and widely used MAC is AppArmor, which, in addition to the features provided by SELinux, includes a learning mode that allows the system to “learn” how a specific application behaves and to set limits by configuring profiles for safe application usage.
In RHEL, SELinux is incorporated into the kernel itself and is enabled in Enforcing mode by default (more on this in the next section), as opposed to Ubuntu, which uses AppArmor.
In this chapter, we will explain the essentials of SELinux and AppArmor and how to use one of these tools for your benefit, depending on your chosen distribution.
Manage SELinux in Linux
Security Enhanced Linux can operate in two different ways:
- Enforcing: SELinux denies access based on SELinux policy rules, a set of guidelines that control the security engine.
- Permissive: SELinux does not deny access, but denials are logged for actions that would have been denied if running in enforcing mode.
SELinux can also be disabled. Although it is not an operation mode itself, it is still an option. However, learning how to use this tool is better than just ignoring it. Keep it in mind!
To display the current mode of SELinux, use getenforce. If you want to toggle the operation mode, use setenforce 0 (to set it to Permissive) or setenforce 1 (Enforcing).
Since this change will not survive a reboot, you will need to edit the /etc/selinux/config file and set the SELINUX variable to either enforcing, permissive, or disabled to achieve persistence across reboots:
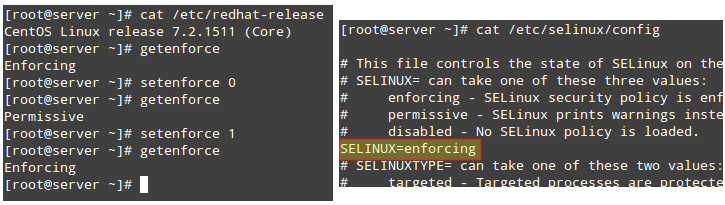
On a side note, if getenforce returns Disabled, you will have to edit /etc/selinux/config with the desired operation mode and reboot. Otherwise, you will not be able to set (or toggle) the operation mode with setenforce.
One of the typical uses of setenforce consists of toggling between SELinux modes (from enforcing to permissive or the other way around) to troubleshoot an application that is misbehaving or not working as expected.
If it works after you set SELinux to Permissive mode, you can be confident you’re looking at a SELinux permissions issue.
Two classic cases where we will most likely have to deal with SELinux are:
- Changing the default port where a daemon listens on.
- Setting the DocumentRoot directive for a virtual host outside of
/var/www/html.
Let’s look at these two cases using the following examples.