Chapter #30: Network Performance, Security, and Troubleshooting
In this chapter, learn how to perform defensive port scanning, secure SSH servers, set up passwordless login, and safely transfer files across your Linux network.

A sound analysis of a computer network begins by understanding what the available tools are to perform the task, how to pick the right one(s) for each step of the way, and finally, where to begin.
In this chapter, we will review some well-known tools to examine the performance and increase the security of a network, as well as what to do when things aren’t going as expected.
What Services are Running and Why?
One of the first things that a system administrator needs to know about each system is what services are running and why. With that information in hand, it is a wise decision to disable all those that are not strictly necessary and avoid hosting too many servers in the same physical machine.
For example, you need to disable your FTP server if your network does not require one (there are more secure methods to share files over a network, by the way). In addition, you should avoid having a web server and a database server in the same system.
If one component becomes compromised, the rest run the risk of getting compromised as well.
Investigating Socket Connections with ss Command
ss is used to dump socket statistics and shows information like netstat, though it can display more TCP and state information than other tools. In addition, it is listed in man netstat as a replacement for netstat, which is obsolete.
However, in this chapter, we will focus on the information related to network security only.
Example 1: List All Open TCP Ports on Your Server
All services running on their default ports (i.e., HTTP on 80, MySQL on 3306) are indicated by their respective names. Others (obscured here for privacy reasons) are shown in their numeric form.
ss -t -a
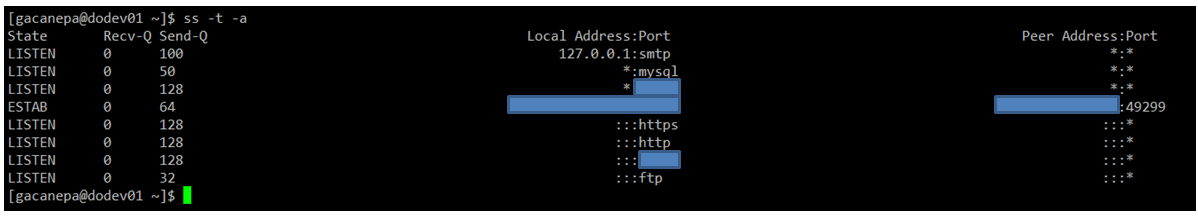
The first column shows the TCP state, while the second and third columns display the amount of data that is currently queued for reception and transmission. The fourth and fifth columns show the source and destination sockets of each connection.
On a side note, you may want to check RFC 793 to refresh your memory about possible TCP states because you also need to check on the number and the state of open TCP connections in order to become aware of (D)DoS attacks.
Example 2: Display All Active TCP Connections and Their Timers
In the output below, you can see that there are 2 established SSH connections. If you notice the value of the second field of timer:, you will notice a value of 36 minutes in the first connection.
ss -t -o
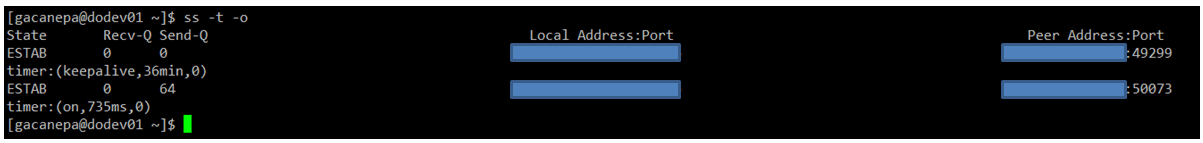
That is the amount of time until the next keepalive probe will be sent. Since it’s a connection that is being kept alive, you can safely assume that it is an inactive connection and thus can kill the process after finding out its PID.
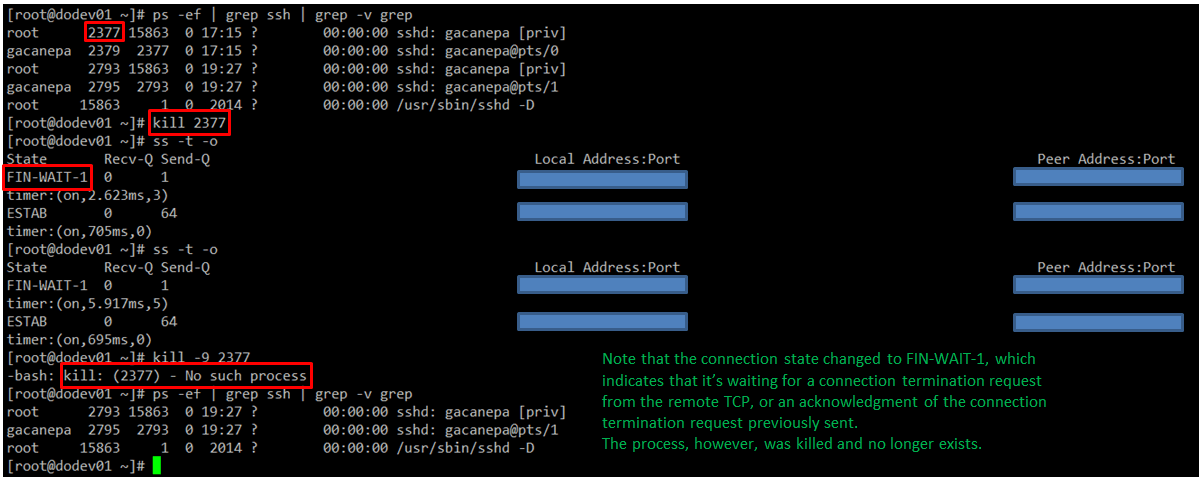
As for the second connection, you can see that it’s currently being used (as indicated by on).
Example 3: Filter Connections by Socket
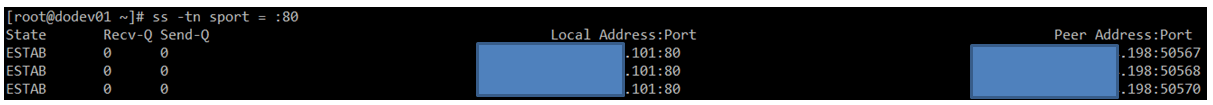
Suppose you want to filter TCP connections by socket. From the server’s point of view, you need to check for connections where the source port is 80.
ss -tn sport = :80