Chapter #26: Encrypted Filesystems and Swap Space
In this chapter, we will discuss how to set up encrypted file systems with dm-crypt (short for device mapper and cryptographic), the standard kernel-level encryption tool.
The idea behind encryption is to allow only trusted persons to access your sensitive data and to protect it from falling into the wrong hands in case of loss or theft of your machine/hard disk.
In simple terms, a key is used to “lock” access to your information so that it becomes available when the system is running and unlocked by an authorized user.
This implies that if a person tries to examine the disk contents (plugging it into his own system or by booting the machine with a Live CD/DVD/USB), he will only find unreadable data instead of the actual files.
Preparing a Drive / Partition / Loop Device for Encryption
Since we will wipe all data present in our chosen drive /dev/sdb, first off, we need to perform a backup of any important files contained in that partition BEFORE proceeding further.
Wipe all data from /dev/sdb. We are going to use dd here, but you could also do it with other tools such as shred. Next, we will create a partition on this device, /dev/sdb1, as we learned in Chapter 4.
dd if=/dev/urandom of=/dev/sdb bs=4096
Testing for Encryption Support
Before we proceed further, we need to make sure that our kernel has been compiled with encryption support:
grep -i config_dm_crypt /boot/config-$(uname -r)
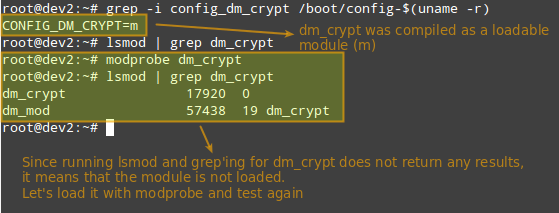
As outlined in the image above, the dm-crypt kernel module needs to be loaded to set up encryption.
Installing Cryptsetup
Cryptsetup is a frontend interface for creating, configuring, accessing, and managing encrypted file systems using dm-crypt.