Chapter #24: The Firewall - iptables, ufw, and firewalld
In this chapter, we explore the fundamentals of Linux firewalls, including how to manage network traffic using iptables, ufw, and firewalld.

You will recall from Chapter 18 ("Network Services") that we gave a basic description of what a firewall is: a mechanism to manage packets coming into and leaving the network.
By “manage,” we mean:
- To allow or prevent certain packets from entering or leaving our network.
- To forward other packets from one point of the network to another.
Based on predetermined criteria.
In this chapter, we will discuss how to implement basic packet filtering and how to configure the firewall with iptables, a frontend to netfilter, which is a native kernel module used for firewalling.
Analogy: The Airport
You can think of a firewall as an international airport where passenger planes come and go almost 24/7. Based on several conditions, such as the validity of a person’s passport or their country of origin (to name a few examples), they may or may not be allowed to enter or leave a certain country.
At the same time, airport officers can instruct people to move from one place of the airport to another if necessary, for example, when they need to go through Customs Services.
We may find the airport analogy useful during the rest of this tutorial. Just keep in mind the following relations as we proceed:
- Persons = Packets
- Firewall = Airport
- Country #1 = Network #1
- Country #2 = Network #2
- Airport regulations enforced by officers = firewall rules
The Basics About iptables
At the low level, it is the kernel itself which “decides” what to do with packets based on rules grouped in chains or sentences.
These chains define what actions should be taken when a packet matches the criteria specified by them.
The first action taken by iptables will consist of deciding what to do with a packet:
- Accept it (let it go through into our network)?
- Reject it (prevent it from accessing our network)?
- Forward it (to another chain)?
Just in case you were wondering why this tool is called iptables, it’s because these chains are organized in tables, with the filter table being the most well-known and the one that is used to implement packet filtering with its three default chains:
- The INPUT chain handles packets coming into our system, which are destined for local programs.
- The OUTPUT chain is used to analyze packets originated in the local network, which are to be sent to the outside.
- The FORWARD chain processes the packets that should be forwarded to another destination (as in the case of a router).
For each of these chains, there is a default policy, which dictates what should be done by default when packets do not match any of the rules in the chain.
You can view the current rules created for each chain and the default policy by running the following command:
iptables -L
The available policies are as follows:
ACCEPT→ lets the packet through. Any packet that does not match any rules in the chain is allowed into the network without questioning.DROP→ drops the packet quietly. Any packet that does not match any rules in the chain is prevented from passing through.REJECT→ rejects the packet and returns an informative message. This one does not work as a default policy. Instead, it is meant to complement packet filtering rules.
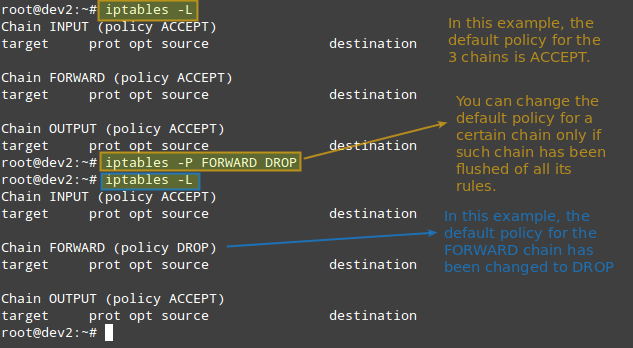
When it comes to deciding which policy you will implement, you need to consider the pros and cons of each approach as explained above. Note that there is no one-size-fits-all solution.