Chapter #18: Configure Ansible Managed Nodes and Run Ad-Hoc Commands
In this chapter, we demonstrate how to set up passwordless SSH access, configure privilege escalation, and use ad-hoc commands for remote system management.
In this chapter, we will demonstrate how you can configure Ansible managed nodes to run ad-hoc commands on remote hosts.
As a recap on our last chapter, managing remote hosts with Ansible requires setting up of Passwordless SSH authentication between the Ansible control node and the managed hosts, which involves the generation of a key pair (Public and Private SSH key pair) on the Ansible Control node and copying the Public key to all of the remote hosts. This will be a crucial step going forward and will make your work much easier.
If you're managing multiple SSH keys, it's recommended to use ssh-agent to load and manage your keys efficiently:
eval $(ssh-agent)
ssh-add ~/.ssh/my_ansible_key
Also, make sure you are aware of the location and format of your Ansible inventory file. By default, Ansible looks at /etc/ansible/hosts. You can specify a custom inventory with the -i flag:
ansible -i my_inventory.ini all -m ping
Configure Privilege Escalation on Managed Nodes
When logged in as a regular user, you may be required to perform certain tasks on managed nodes that require elevated privileges or root privileges.
These tasks include package management, adding new users & groups, and modifying system configurations to mention just but a few.
To achieve this, you need to invoke certain directives in the playbook to run the tasks as a privileged user on the remote hosts.
Using become to Gain Root Privileges
Ansible allows you to ‘become’ another user on the managed node different from the one currently logged in. The become: yes directive elevates your privileges and allows you to perform tasks that require root privileges such as installing and updating packages and rebooting the system.
Consider a playbook httpd.yml that installs and starts Apache webserver as shown:
---
- name: install and start Apache webserver
hosts: webservers
tasks:
- name: install httpd
yum: name=httpd state=latest
become: yes
- name: check httpd status
service: name=httpd state=started
The become: yes directive allows you to execute commands as a root user on the remote host.
Using become_user to Switch to a Different User
Another directive that you can use to become another user is the become_user. This allows you to switch to a sudo user on the remote host upon logging in and not the user you log in as.
For example, to run a command as tecmint user on the remote use the directive as shown.
- name: Run a command as the apache user
command: somecommand
become: yes
become_user: tecmint
Using become_method to Specify the Privilege Escalation Mechanism
This directive will override the default method set in the ansible.cfg file, which is usually set to sudo. You can use it to specify alternatives like su, pbrun, or doas.
For example, to switch to the nobody user using the su method, you can run the following task:
- name: Run a command as nobody using su
command: somecommand
become: true
become_method: su
become_user: nobody
Using become_flags to Customize Privilege Escalation Behavior
The become_flags directive is used to pass extra options or arguments to the privilege escalation command (like sudo or su). It lets you customize how the switch to another user is performed during a task or play.
This can be especially useful in situations where the target user account has restricted access like when the shell is set to /sbin/nologin or /usr/sbin/nologin, meaning the user cannot normally log in.
For example, the user nobody typically has a non-interactive shell, so running commands directly as that user would fail. To work around this, you can specify a different shell (like /bin/sh) using become_flags.
- name: Run a command as nobody
command: somecommand
become: true
become_method: su
become_user: nobody
become_flags: '-s /bin/sh'
Command-line Options in Privilege Escalation
Let’s take a look at some of the command-line options that you can use to elevate your privileges when running commands:
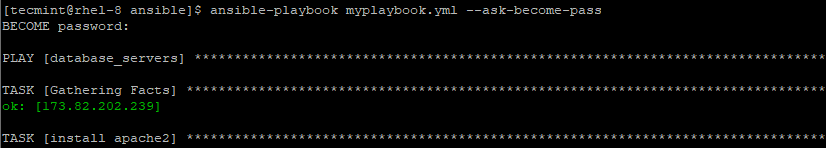
--ask-become-pass, -K - This prompts you for the password of the sudo user on the remote system that you are trying to connect.
ansible-playbook myplaybook.yml --ask-become-pass
--become, -b - This allows you to run the task as a root user without prompting for a password.
ansible-playbook myplaybook.yml --become
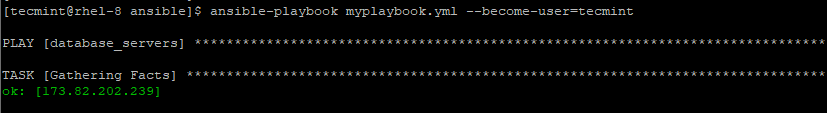
--become-user=BECOME_USER - It allows you to run tasks as another user.
ansible-playbook myplaybook.yml --become-user=tecmint